32 Bit Hex Encryption Key Generator
There are multiple ways of generating an encryption key. Most implementations rely on a random object. All examples mentioned here use a secure cryptographic randomizer. The parts of the key should each be a single hex number, while the cryptotext should be a sequence of bytes. Here are some acceptable (equivalent) examples for the cryptotext: 0x12 0x34 0x56 0x78; 12 34 56 78. Key Generation. To generate a key pair, just click the Generate button. This will generate a 1024 bit key. There's also a random letter generator that you may prefer. Hash Generator. For random MD5 strings, set the base to 16 (hexadecimal) and the length to 32 characters. Internet download manager license key generator. For random SHA-1 hash strings, set the base to 16 (hexadecimal) and the length to 40 characters. For a 128 bit WEP network password, use. The Firewall.cx Wireless LAN Key Generator will allow the generation of a WEP or WPA ASCII based encryption key and will provide the equivalent HEX or ASCII string so it can be inserted directly into a Cisco Access Point configuration. Oct 05, 2016 Generate truly random cryptographic keys using a random number generator in.NET. In case you need a random value to be used in cryptography such as a cryptographic key in symmetric and asymmetric encryption then System.Random is not an acceptable. Cryptographic algorithms require keys of specific length such as 32-bit or 256-bit keys.
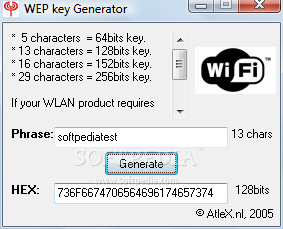
About the WLAN Key Generator
The SG WLAN Key Generator is a tool that allows for quick, valid, and strong WEP/WPA key generation. It uses the 94 standard ASCII characters (with codes 32 to 126) for maximum compatability.
To generate a random WEP or WPA key, simply choose the desired key length and one will be generated for you. To generate a key based on a custom passphrase, enter your phrase into either the Custom Key text fields, and its HEX or ASCII equivalent will be generated for you automatically in the other custom text field.
To use any of the generated WEP keys, simply right-click on the appropriate text field (highlight the text if necessary), then choose copy from the pull-down menu, and paste the text whesre applicable.
Xiao Ling / February 27, 2014 October 29, 2019 / Security / C/C, OpenSSL, RSA 5 comments It is known that RSA is a cryptosystem which is used for the security of data transmission. This tutorial introduces how to use RSA to generate a pair of public and private keys on Windows. I'm trying to generate every time same RSA key with RSAgeneratekeyex(.) and then write in file, but I always get different keys. Is there any turnkey solution or I need to write my own function for this? (I know that this is unsecure solution). Rsa_generate_key_ex c r.
32 Bit Hex Encryption Key Generator For Sale
Notes: WEP encryption uses 24 bit 'Initilization Vector' in addition to the 'secret key'. Therefore, 40 bit WEP can be refered to as 64 bit WEP, and 104 bit can be referedo to as 128 bit, depending on whether the 'initialization vector' is counted or not.
- Security Scanner » Ports Database » Vulnerable Ports » Commonly Open Ports
40-bit encryption refers to a key size of forty bits, or five bytes, for symmetric encryption; this represents a relatively low level of security. A forty bit length corresponds to a total of 240 possible keys. Although this is a large number in human terms (about a trillion), it is possible to break this degree of encryption using a moderate amount of computing power in a brute-force attack, i.e., trying out each possible key in turn.
Description[edit]
A typical home computer in 2004 could brute-force a 40-bit key in a little under two weeks, testing a million keys per second; modern computers are able to achieve this much faster. Using free time on a large corporate network or a botnet would reduce the time in proportion to the number of computers available.[1] With dedicated hardware, a 40-bit key can be broken in seconds. The Electronic Frontier Foundation's Deep Crack, built by a group of enthusiasts for US$250,000 in 1998, could break a 56-bit Data Encryption Standard (DES) key in days,[2] and would be able to break 40-bit DES encryption in about two seconds.[3]
40-bit encryption was common in software released before 1999, especially those based on the RC2 and RC4 algorithms which had special '7-day' export review policies,[citation needed] when algorithms with larger key lengths could not legally be exported from the United States without a case-by-case license. 'In the early 1990s .. As a general policy, the State Department allowed exports of commercial encryption with 40-bit keys, although some software with DES could be exported to U.S.-controlled subsidiaries and financial institutions.'[4][5] As a result, the 'international' versions of web browsers were designed to have an effective key size of 40 bits when using Secure Sockets Layer to protect e-commerce. Similar limitations were imposed on other software packages, including early versions of Wired Equivalent Privacy. In 1992, IBM designed the CDMF algorithm to reduce the strength of 56-bit DES against brute force attack to 40 bits, in order to create exportable DES implementations.

Obsolescence[edit]
All 40-bit and 56-bit encryption algorithms are obsolete, because they are vulnerable to brute force attacks, and therefore cannot be regarded as secure.[6][7] As a result, virtually all Web browsers now use 128-bit keys, which are considered strong. Most Web servers will not communicate with a client unless it has 128-bit encryption capability installed on it.
Public/private key pairs used in asymmetric encryption (public key cryptography), at least those based on prime factorization, must be much longer in order to be secure; see key size for more details.
As a general rule, modern symmetric encryption algorithms such as AES use key lengths of 128, 192 and 256 bits.
See also[edit]
Footnotes[edit]
- ^Schneier 1996, p. 154.
- ^EFF-1998.
- ^Schneier 1996, p. 153.
- ^Grimmett 2001.
- ^Schneier 1996, p. 615.
- ^University of California at Berkeley Public Information Office (January 29, 1997). 'The only legally exportable cryptography level is totally insecure; UC Berkeley grad student breaks challenge cipher in hours'. The Regents of the University of California. Retrieved December 14, 2015.
This is the final proof of what we've known for years: 40-bit encryption technology is obsolete.
- ^Fitzmaurice, Ellen; Tamaki, Kevin (June 1, 1997). 'Decoding the Encryption Debate: U.S. export restrictions and 'key recovery' policies are ineffectual as well as burdensome to business'. Los Angeles Times. Retrieved December 14, 2015.
But recent advances in computing technology have rendered 40-bit encryption dangerously weak and export limits commercially obsolete.
References[edit]
- 'Frequently Asked Questions (FAQ) About the Electronic Frontier Foundation's 'DES Cracker' Machine'. Electronic Frontier Foundation. July 16, 1998. Archived from the original on September 18, 2012. Retrieved March 23, 2012.
- Grimmett, Jeanne J. (2001). Encryption Export Controls(pdf) (Report). Congressional Research Service Report RL30273.
- Schneier, Bruce (1996). Applied Cryptography (Second ed.). John Wiley & Sons. ISBN0-471-11709-9.