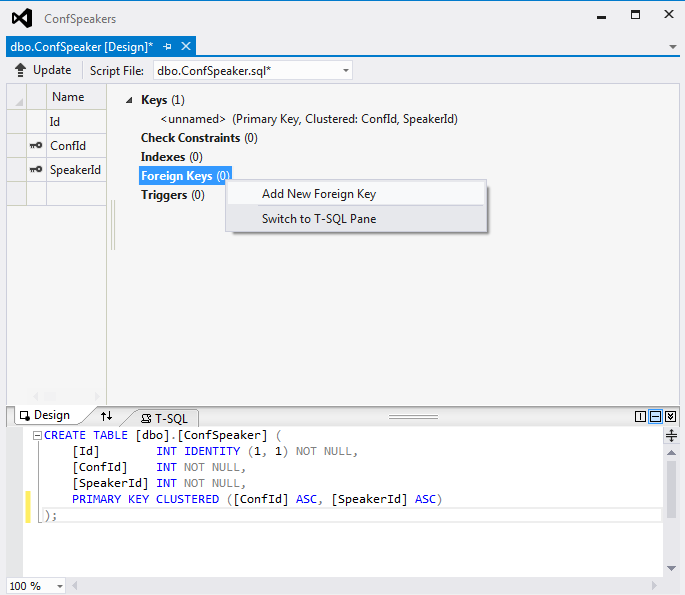
Visual Studio Generate Temporary Key
If you want to publish an application by using ClickOnce deployment, the application and deployment manifests must be signed with a public/private key pair and signed using Authenticode technology. You can sign the manifests by using a certificate from the Windows certificate store or a key file.
For more information about ClickOnce deployment, see ClickOnce security and deployment.
Signing the ClickOnce manifests is optional for .exe-based applications. For more information, see the 'Generate unsigned manifests' section of this document.
For information about creating key files, see How to: Create a public-private key pair.
Microsoft Visual Studio is a valuable tool that is capable of developing everything from software to websites. But with its popularity comes the risk of criminals and hackers taking advantage of our better nature by using it to design malware and other dangerous content. Use the Visual Studio manifest designer to configure the package. For example, add tile images and choose the orientations your app supports. Generate an app package. Use the Visual Studio packaging wizard to create an app package. Run, debug, and test a packaged application. Run and debug your app package from Visual Studio or by installing. You must have a cryptographic key pair to sign an assembly with a strong name. For more information about creating a key pair, see How to: Create a public-private key pair. Create and sign an assembly with a strong name by using Visual Studio. In Solution Explorer, open the shortcut menu for the project, and then choose Properties.
Note
Visual Studio supports only Personal Information Exchange (PFX) key files that have the .pfx extension. However, you can select other types of certificates from the current user's Windows certificate store by clicking Select from Store on the Signing page of project properties.
Sign using a certificate
Go to the project properties window (right-click the project node in Solution Explorer and select Properties). On the Signing tab, select the Sign the ClickOnce manifests check box.
Click the Select from Store button.
The Select a Certificate dialog box appears and displays the contents of the Windows certificate store.
Tip
If you click Click here to view certificate properties, the Certificate Details dialog box appears. This dialog box includes detailed information about the certificate and additional options. Click Certificates to view additional help information.
Select the certificate that you want to use to sign the manifests.
Additionally, you can specify the address of a timestamp server in the Timestamp server URL text box. This is a server that provides a timestamp specifying when the manifest was signed.
Sign using an existing key file

On the Signing page, select the Sign the ClickOnce manifests check box.
Click the Select from File button.
The Select File dialog box appears.
Api key for google. Apr 10, 2020 To get an API key: Go to the Google Cloud Platform Console. Click the project drop-down and select or create the project for which you want to add an API key. Click the menu button and select APIs & Services Credentials. On the Credentials page, click Create credentials API key. The API key created dialog displays your newly created API key.
In the Select File dialog box, browse to the location of the key file (.pfx) that you want to use, and then click Open.
Note
This option supports only files that have the .pfx extension. If you have a key file or certificate in another format, store it in the Windows certificate store and select the certificate is described in the previous procedure. The selected certificate's purpose should include code signing.
The Enter password to open file dialog box appears. (If the .pfx file is already stored in your Windows certificate store or is not password protected, you aren't prompted to enter a password.)
Enter the password to access the key file, and then select Enter.
Note
The .pfx file cannot include certificate chaining information. If it does, the following import error will occur: Cannot find the certificate and private key for decryption. To remove the certificate chaining information, you can use Certmgr.msc and disable the option to Include all certificates when exporting the *.pfx file.
Sign using a test certificate
On the Signing page, select the Sign the ClickOnce manifests check box.
To create a new certificate for testing, click the Create Test Certificate button.
In the Create Test Certificate dialog box, enter a password to help secure your test certificate.
Generate unsigned manifests
Signing the ClickOnce manifests is optional for .exe-based applications. The following procedures show how to generate unsigned ClickOnce manifests.
Important
Unsigned manifests can simplify development and testing of your application. However, unsigned manifests introduce substantial security risks in a production environment. Only consider using unsigned manifests if your ClickOnce application runs on computers within an intranet that is completely isolated from the internet or other sources of malicious code.
By default, ClickOnce automatically generates signed manifests unless one or more files are specifically excluded from the generated hash. In other words, publishing the application results in signed manifests if all files are included in the hash, even when the Sign the ClickOnce manifests check box is cleared.
To generate unsigned manifests and include all files in the generated hash
To generate unsigned manifests that include all files in the hash, you must first publish the application together with signed manifests. Therefore, first sign the ClickOnce manifests by following one of the previous procedures, and then publish the application.
On the Signing page, clear the Sign the ClickOnce manifests check box.
Reset the publish version so that only one version of your application is available. By default, Visual Studio automatically increments the revision number of the publish version every time that you publish an application. For more information, see How to: Set the ClickOnce publish version.
Publish the application.
To generate unsigned manifests and exclude one or more files from the generated hash
On the Signing page, clear the Sign the ClickOnce manifests check box.
Open the Application Files dialog box and set the Hash to Exclude for the files that you want to exclude from the generated hash.
Note
Excluding a file from the hash configures ClickOnce to disable automatic signing of the manifests, so you do not need to first publish with signed manifests as shown in the previous procedure.
Publish the application.
See also
-->This article explains how to create and export a certificate for app package signing using PowerShell tools. It's recommended that you use Visual Studio for packaging UWP apps and packaging desktop apps, but you can still package an app manually if you did not use Visual Studio to develop your app.
Prerequisites
A packaged or unpackaged app
An app containing an AppxManifest.xml file. You will need to reference the manifest file while creating the certificate that will be used to sign the final app package. For details on how to manually package an app, see Create an app package with the MakeAppx.exe tool.Public Key Infrastructure (PKI) Cmdlets
You need PKI cmdlets to create and export your signing certificate. For more information, see Public Key Infrastructure Cmdlets.
Create a self-signed certificate
A self-signed certificate is useful for testing your app before you're ready to publish it to the Store. Follow the steps outlined in this section to create a self-signed certificate.
Note
When you create and use a self-signed certificate only users who install and trust your certificate can run your application. This is easy to implement for testing but it may prevent additional users from installing your application. When you are ready to publish your application we recommend that you use a certificate issued by a trusted source. This system of centralized trust helps to ensure that the application ecosystem has levels of verification to protect users from malicious actors.
Determine the subject of your packaged app
To use a certificate to sign your app package, the 'Subject' in the certificate must match the 'Publisher' section in your app's manifest.
For example, the 'Identity' section in your app's AppxManifest.xml file should look something like this:
The 'Publisher', in this case, is 'CN=Contoso Software, O=Contoso Corporation, C=US' which needs to be used for creating your certificate.
Use New-SelfSignedCertificate to create a certificate
Use the New-SelfSignedCertificate PowerShell cmdlet to create a self signed certificate. New-SelfSignedCertificate has several parameters for customization, but for the purpose of this article, we'll focus on creating a simple certificate that will work with SignTool. For more examples and uses of this cmdlet, see New-SelfSignedCertificate.
Based on the AppxManifest.xml file from the previous example, you should use the following syntax to create a certificate. In an elevated PowerShell prompt:
Note the following details about some of the parameters:
KeyUsage: This parameter defines what the certificate may be used for. For a self-signing certificate, this parameter should be set to DigitalSignature.
TextExtension: This parameter includes settings for the following extensions:
Extended Key Usage (EKU): This extension indicates additional purposes for which the certified public key may be used. For a self-signing certificate, this parameter should include the extension string '2.5.29.37={text}1.3.6.1.5.5.7.3.3', which indicates that the certificate is to be used for code signing.
Basic Constraints: This extension indicates whether or not the certificate is a Certificate Authority (CA). For a self-signing certificate, this parameter should include the extension string '2.5.29.19={text}', which indicates that the certificate is an end entity (not a CA).
After running this command, the certificate will be added to the local certificate store, as specified in the '-CertStoreLocation' parameter. The result of the command will also produce the certificate's thumbprint.
You can view your certificate in a PowerShell window by using the following commands:
This will display all of the certificates in your local store.
Export a certificate
Visual Studio Product Keys
To export the certificate in the local store to a Personal Information Exchange (PFX) file, use the Export-PfxCertificate cmdlet.
When using Export-PfxCertificate, you must either create and use a password or use the '-ProtectTo' parameter to specify which users or groups can access the file without a password. Note that an error will be displayed if you don't use either the '-Password' or '-ProtectTo' parameter.
Password usage
ProtectTo usage
Microsoft Visual Studio Product Key
After you create and export your certificate, you're ready to sign your app package with SignTool. For the next step in the manual packaging process, see Sign an app package using SignTool.
Security considerations
By adding a certificate to local machine certificate stores, you affect the certificate trust of all users on the computer. It is recommended that you remove those certificates when they are no longer necessary to prevent them from being used to compromise system trust.